The Universal
Cloud Terminal
Manage Azure, GCP, AWS, Hetzner, and Vultr servers from a single, blazing-fast TUI. Rent, manage, and SSH in seconds.
Shareware-era simple: distribute, trial, license, own.
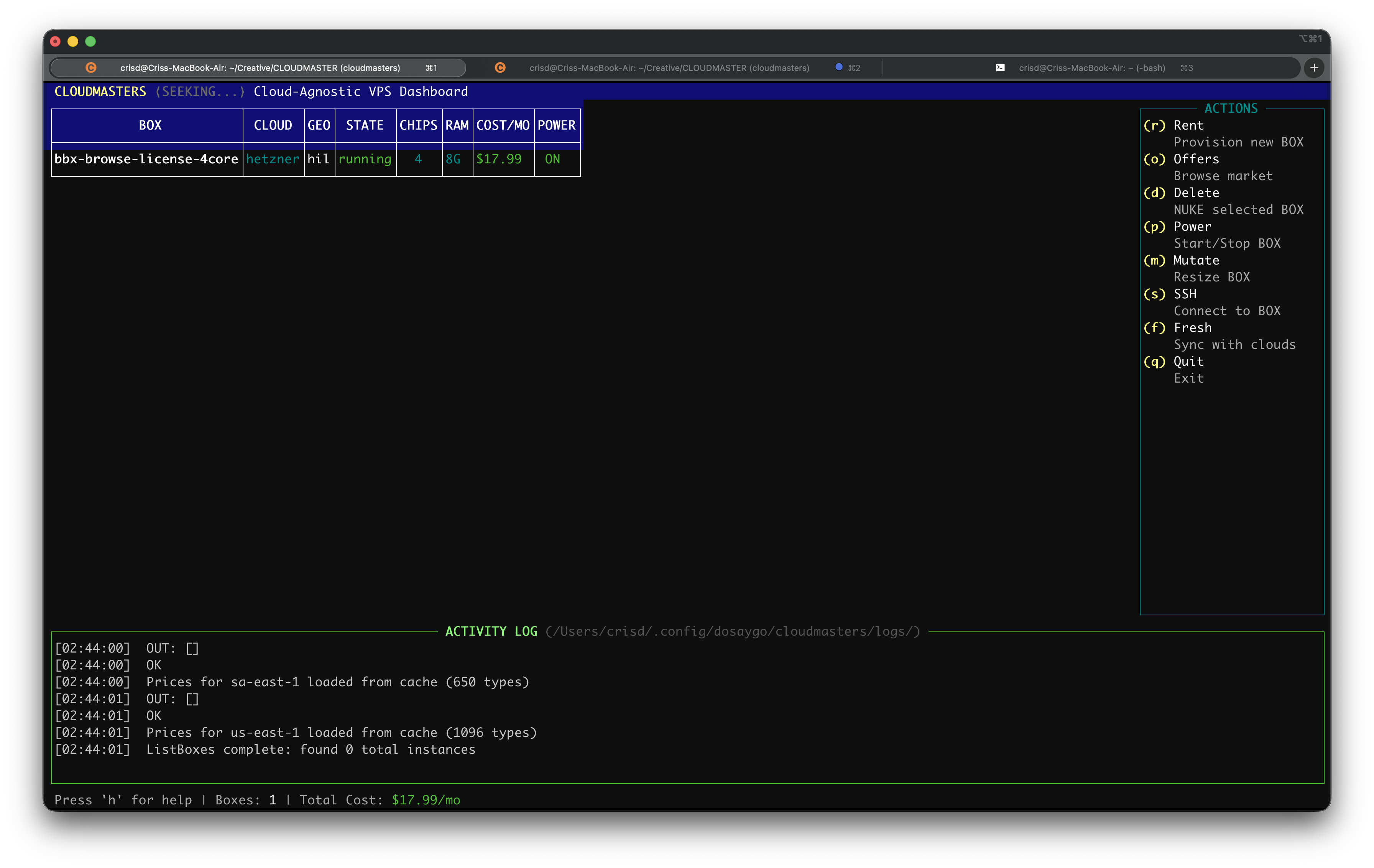
Manage Azure, GCP, AWS, Hetzner, and Vultr servers from a single, blazing-fast TUI. Rent, manage, and SSH in seconds.
Shareware-era simple: distribute, trial, license, own.

macOS (.pkg), Windows (.exe), Linux (.tar.gz), or the curl/bash installer.
Use the GUI installer or PowerShell to bootstrap fast.
One-liner installer for quick starts and headless boxes.
Wraps official CLIs (az, gcloud, hcloud, aws) for stable, authenticated access without managing new secrets.
Built with tview and Go. Keyboard-driven navigation, instant search, and real-time status updates.
Compare prices across providers instantly. Sort by CPU, RAM, and price to find the best deal for your workload.
Zero telemetry by default. Your credentials stay on your machine. Direct SSH access with automatic key management.
Servers grouped by 15 canonical cities worldwide. No more guessing which "us-east" is which.
Launch Docker, NGINX, or VNC desktops with pre-configured cloud-init scripts and firewall rules.
We built CloudMasters for people who have been burned by surveillance software. Your data and IP are yours, forever.
We never claim ownership of your infrastructure, configs, or code. What you build stays yours, period.
CloudMasters sits on top of official CLIs. We don’t receive or store your cloud credentials.
Activity logs are designed for security and support, not surveillance. They avoid secrets and focus on timestamps and actions.
Try it free, license when it pays for itself, and keep your workflows forever.
Follow the release feed